For the most part, we are providing the complete research assistance for the research scholars. This article is about the depiction of permitting the python bindings in network simulator 3.
Phase: I
At first, we have to develop the python bindings based on network simulator 3 through the utilization of the novel tool which is named as the PyBindGen.
Phase: II
As the next process, we have to configure the python process through the implementation of the following commands.
./waf –disable-python
/usr/bin/python2.6 ./waf configure
Phase: III
Consequently, we have to implement the python code over the utilization of the following commands.
./waf shell

python scratch/mixed-wireless.py
or
sudo ./waf –pyrun scratch/mixed-wireless.py

Finally, we have demonstrated the result that is acquired through the implementation of the command that is highlighted above.
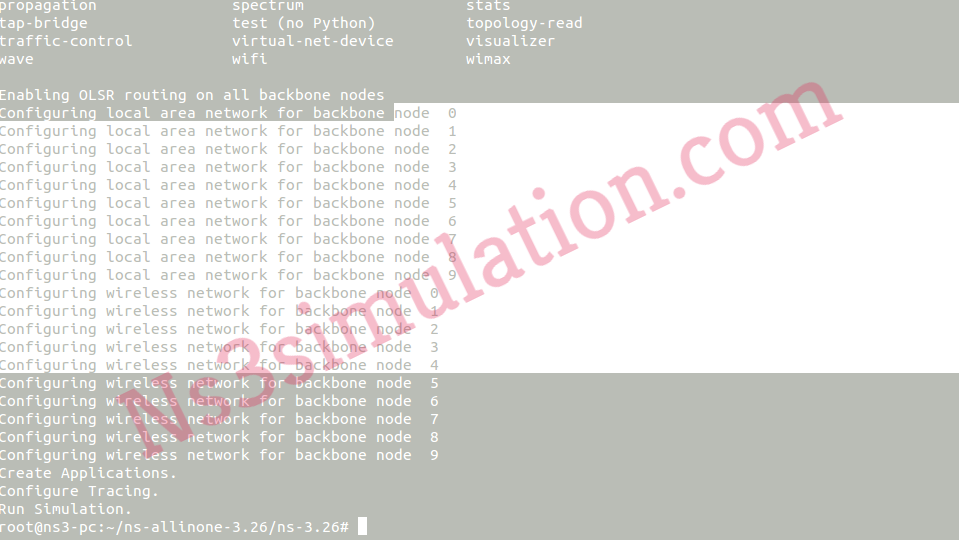
To this end, we hope that we have delivered the enough knowledge about the process of enabling python bindings in Ns3. Additionally, the researchers can ping us and acquire more research assistance!!!














