PHD in NS3 Simulation Handling different kind of networking attack is one of the prominent research scopes of the PhD researchers. In this PHD in NS3 simulation we are going to be discussing about the attack in different networks.
Networking attack in MANET:
- Security in mobile ADHOC network is a big challenge as it has no centralized authority which can supervise the individual nodes operating in the network.
- The attacks can come from both inside the network and from the outside.
Vulnerability of MANET:
- Cooperativeness.
- Limited power supply.
- Lack of centralized management.
- Dynamic topology.
- Resource availability.
- Scalability.
- No predefined boundary.
- Bandwidth constraint.
- Adversary inside the attack.
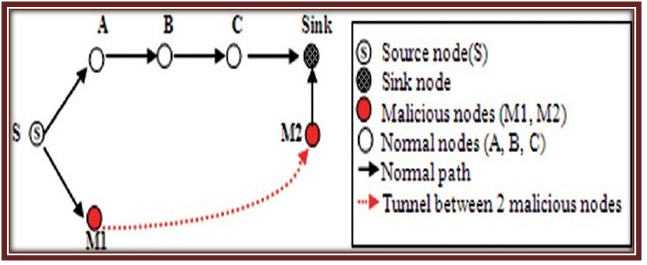
Architecture of attack in MANET:
Security goals of MANET:
- Authentication.
- Non repudiation.
- Availability.
- Anonymity.
- Integrity.
- Authorization.
- Confidentiality.
Classification of attacks in manet:
Generally in manet attacks are classified into active attack, passive attack, internal attack and external attack. Major classification as follows,
- CONTROL traffic attack.
- Cooperative blackmail.
- Bogus registration.
- Rushing.
- Worm-hole.
- Blackmail.
- HELLO flood.
- Cache poisoning.
- sybil.
- Man in middle attack.
- DATA traffic attack.
- Jellyfish.
- Black-hole.
- Cooperative black-hole.
- Gray-hole attack.
Sample code for attack in MANET:
std::string rate ("2048bps"); std::string phyMode ("DsssRate11Mbps"); std::string tr_name ("manet-routing-attack"); int nodeSpeed = 45; //in m/s int nodePause = 1; //in s m_protocolName = "protocol"; Config::SetDefault  ("ns3::OnOffApplication::PacketSize",StringValue ("64")); Config::SetDefault ("ns3::OnOffApplication::DataRate",  StringValue (rate)); NqosWifiMacHelper wifiMac = NqosWifiMacHelper::Default (); wifi.SetRemoteStationManager ("ns3::ConstantRateWifiManager", "DataMode",StringValue (phyMode), "ControlMode",StringValue (phyMode)); wifiPhy.Set ("TxPowerStart",DoubleValue (txp)); wifiPhy.Set ("TxPowerEnd", DoubleValue (txp)); wifiMac.SetType ("ns3::AdhocWifiMac"); NetDeviceContainer adhocDevices = wifi.Install (wifiPhy, wifiMac, adhocNodes); MobilityHelper mobilityAdhoc; int64_t streamIndex = 0; // used to get consistent mobility across scenarios ObjectFactory pos; pos.SetTypeId ("ns3::RandomRectanglePositionAllocator"); pos.Set ("X", StringValue ("ns3::UniformRandomVariable[Min=0.0|Max=300.0]")); pos.Set ("Y", StringValue ("ns3::UniformRandomVariable[Min=0.0|Max=1500.0]")); Ptr<PositionAllocator> taPositionAlloc = pos.Create ()->GetObject<PositionAllocator> (); streamIndex += taPositionAlloc->AssignStreams (streamIndex); std::stringstream ssSpeed; ssSpeed << "ns3::UniformRandomVariable[Min=0.0|Max=" << nodeSpeed << "]"; std::stringstream ssPause; ssPause << "ns3::ConstantRandomVariable[Constant=" << nodePause << "]"; mobilityAdhoc.SetMobilityModel ("ns3::RandomWaypointMobilityModel", "Speed", StringValue (ssSpeed.str ()), "Pause", StringValue (ssPause.str ()), "PositionAllocator", PointerValue (taPositionAlloc)); mobilityAdhoc.SetPositionAllocator (taPositionAlloc); mobilityAdhoc.Install (adhocNodes); streamIndex += mobilityAdhoc.AssignStreams (adhocNodes, streamIndex) OnOffHelper onoff1 ("ns3::UdpSocketFactory",Address ()); onoff1.SetAttribute ("OnTime", StringValue ("ns3::ConstantRandomVariable[Constant=1.0]")); onoff1.SetAttribute ("OffTime", StringValue ("ns3::ConstantRandomVariable[Constant=0.0]"));Attack in sensor network:
- Majority of the sensor network are deployed in hostile environments with active intelligent opposition. Hence security is a crucial issue.
Security goals in wsn:
Majorly the security goals are divided into two categories like primary goal and secondary goal.
- Primary goals.
- Data integrity.
- Data availability.
- Data confidentiality.
- Data authentication.
- Secondary goals.
- Secure localization.
- Time synchronization.
- Data freshness.
- Self-organization.
Types of attack in WSN:
- Physical attack.
- Node replication attacks.
- Node outage.
- Passive information gathering.
- Message corruption.
- Attack against privacy.
- Camouflages adversaries.
- Monitor & Eaves dropping.
- Traffic analysis.
- False node.
- Node malfunction.
- DoS.
- Other routing attacks.
- HELLO flood.
- Spoofed, altered & replayed routing information.
- Wormhole.
- Selective forwarding.
- Sybil.
- Sinkhole attack.
- Node subversion.
Sample code for attack in WSN:
std::string rate ("2048bps");
std::string phyMode ("DsssRate11Mbps");
std::string tr_name ("manet-routing-attack");
int nodeSpeed = 45; //in m/s
int nodePause = 1; //in s
m_protocolName = "protocol";
Config::SetDefault  ("ns3::OnOffApplication::PacketSize",StringValue ("64"));
Config::SetDefault ("ns3::OnOffApplication::DataRate",  StringValue (rate));
NqosWifiMacHelper wifiMac = NqosWifiMacHelper::Default ();
wifi.SetRemoteStationManager ("ns3::ConstantRateWifiManager",
"DataMode",StringValue (phyMode),
"ControlMode",StringValue (phyMode));
wifiPhy.Set ("TxPowerStart",DoubleValue (txp));
wifiPhy.Set ("TxPowerEnd", DoubleValue (txp));
wifiMac.SetType ("ns3::AdhocWifiMac");
NetDeviceContainer adhocDevices = wifi.Install (wifiPhy, wifiMac, adhocNodes);
MobilityHelper mobilityAdhoc;
int64_t streamIndex = 0; // used to get consistent mobility across scenarios
ObjectFactory pos;
pos.SetTypeId ("ns3::RandomRectanglePositionAllocator");
pos.Set ("X", StringValue ("ns3::UniformRandomVariable[Min=0.0|Max=300.0]"));
pos.Set ("Y", StringValue ("ns3::UniformRandomVariable[Min=0.0|Max=1500.0]"));
Ptr<PositionAllocator> taPositionAlloc = pos.Create ()->GetObject<PositionAllocator> ();
streamIndex += taPositionAlloc->AssignStreams (streamIndex);
std::stringstream ssSpeed;
ssSpeed << "ns3::UniformRandomVariable[Min=0.0|Max=" << nodeSpeed << "]";
std::stringstream ssPause;
ssPause << "ns3::ConstantRandomVariable[Constant=" << nodePause << "]";
mobilityAdhoc.SetMobilityModel ("ns3::RandomWaypointMobilityModel",
"Speed", StringValue (ssSpeed.str ()),
"Pause", StringValue (ssPause.str ()),
"PositionAllocator", PointerValue (taPositionAlloc));
mobilityAdhoc.SetPositionAllocator (taPositionAlloc);
mobilityAdhoc.Install (adhocNodes);
streamIndex += mobilityAdhoc.AssignStreams (adhocNodes, streamIndex)
OnOffHelper onoff1 ("ns3::UdpSocketFactory",Address ());
onoff1.SetAttribute ("OnTime", StringValue ("ns3::ConstantRandomVariable[Constant=1.0]"));
onoff1.SetAttribute ("OffTime", StringValue ("ns3::ConstantRandomVariable[Constant=0.0]"));NodeContainer c; // ALL Nodes
NodeContainer not_malicious;
NodeContainer malicious;
c.Create(4);
not_malicious.Add(c.Get(1));
not_malicious.Add(c.Get(2));
not_malicious.Add(c.Get(3));
malicious.Add(c.Get(0));
InternetStackHelper internet;
internet.SetRoutingHelper (aodv);
internet.Install (not_malicious);
malicious_aodv.Set("IsMalicious",BooleanValue(true)); // putting *false* instead of *true* would diable the malicious behavior of the node
internet.SetRoutingHelper (malicious_aodv);
internet.Install (malicious);
monitor->CheckForLostPackets ();
Ptr<Ipv4FlowClassifier> classifier = DynamicCast<Ipv4FlowClassifier> (flowmon.GetClassifier ());
std::map<FlowId, FlowMonitor::FlowStats> stats = monitor->GetFlowStats ();
for (std::map<FlowId, FlowMonitor::FlowStats>::const_iterator i = stats.begin (); i != stats.end (); ++i)
{
Ipv4FlowClassifier::FiveTuple t = classifier->FindFlow (i->first);
if ((t.sourceAddress=="10.1.2.2" && t.destinationAddress == "10.1.2.4"))
{
std::cout << "Flow " << i->first  << " (" << t.sourceAddress << " -> " << t.destinationAddress << ")\n";
std::cout << "  Tx Bytes:   " << i->second.txBytes << "\n";
std::cout << "  Rx Bytes:   " << i->second.rxBytes << "\n";
std::cout << "  Throughput: " << i->second.rxBytes * 8.0 / (i->second.timeLastRxPacket.GetSeconds() - i->second.timeFirstTxPacket.GetSeconds())/1024/1024  << " Mbps\n";
}
}
monitor->SerializeToXmlFile("lab-4.flowmon", true, true);